|
By H. Taz Daughtrey and Randall Rice, CTAL Full, CTFL-AT, CMT
The villain threatens our hero with the menacing "We can do this the easy way, or we can do this the hard way."
What the villain wants is some information our hero is reluctant to reveal. The "easy way" is for our hero to relent and share the secret. The "hard way" implies some pain will be inflicted in attempting to extract the information.
Safeguarding computerized data is a similar challenge, with plenty of villains trying to pry loose the information. In this case, although the "easy way" is initially painless, it is not truly easy or painless. The villain infiltrates our hero's system and happily does his worst, often undetected for weeks and months. Only when the breach has been discovered and the losses tallied does the pain begin.
The "easy way" of neglecting security - or neglecting to assess security - is sure to lead to payment later, often in the most unscheduled and unbudgeted manner. Paying - or rather investing - upfront in security measures may seem the "hard way" but in the end should spare much of the pain that would otherwise be felt.
What have you got to lose?
Security breaches are derelictions of duty ... the duty to safeguard what was entrusted to you.
Security breaches cost, both in monetary and reputational terms.
Security breaches invariably make the headlines.
Security breaches may put you out of business.
For example, if your business needs to comply with the Payment Card Industry (PCI) Data Security Standard, some but not all of the monetary costs may come from:
- a mandatory forensic examination
- notification of customers
- credit monitoring for affected customers
- PCI compliance fines
- liability for fraud charges
- card replacement costs
- upgrade or replacement of POS system
- reassessment for PCI compliance.
On the non-monetary side, ongoing costs may accumulate from:
- damage to your brand and business reputation
- bad publicity that will probably persist indefinitely in social media
- loss of payment card privileges
- your time and attention.
In a 2014 study on breach notification [1], 57% of the people who had received a breach notification letter from a business said they lost trust and confidence in the organization. Worse, 29% of those surveyed said they terminated their relationship with the responsible organization.
Commissioner Luis A. Aguilar of the U.S. Securities and Exchange Commission reports [2] that small and medium-sized businesses (SMB) are finding it increasingly difficult to recover from attacks. He cites a National Small Business Association survey [3] that a growing number (up to 33 percent) of firms take at least three days to recover from an attack. And, in an especially dispiriting development, the survey found that SMBs that were the victims of a cyberattack were more likely to be targeted again. A not-insignificant proportion (some [4] claim as much as 60 percent) of small firms go out of business within six months of a data breach.
What's the Problem?
The novelty and difficulty of the problem can be illustrated by considering the source of defects in software. Traditionally, software quality practitioners, including testers, have dealt only with accidentally injected defects that will be discovered accidentally, that is in the normal course of using the system. The assurance task has been first to prevent and then to detect and remove such defects before the user encounters them.
But now malicious agents are seeking out these accidentally injected defects. These are the bad actors who seek to exploit buffer overflows or lack of input checking for their own purposes. More worryingly, defects are being injected deliberately. Whether they then intend to take advantage of these vulnerabilities themselves or wait for an unsuspecting user to trigger some exploit, software quality is definitely endangered.
These bad actors are mastering ever-more subtle and successful ways to highjack, pervert, or plunder computer-based resources. Their criminal activity takes many forms such as extortion through ransomware or disruption through defacement or denial-of-service attacks. And it always seems the offense is a step or two ahead of defensive measures. Software no longer simply "breaks on its own," and those who depend on it must be aware of, and responsive to, these attacks.
What is to be done?
Is it enough to add explicit security requirements and then test against them? Can anyone elaborate all the cases where one specifies "The software shall not do thus-and-so under such-and-such conditions"? Unlikely in the extreme.
As illustrated below, most acceptable behaviors of a system can be specified, but the full range of unacceptable behaviors is beyond practical enumeration. Thus security testing has to mean much more than simply testing against security requirements.
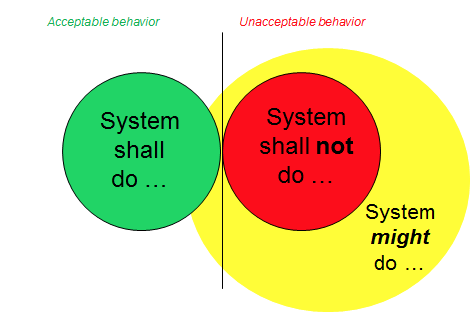
Testing can provide a significant contribution to the assurance of system acceptability. Yet its value is greatly dependent on the capabilities of those designing and conducting the tests. As systems become more complex and more dependent on the (essentially invisible) element of software, specialized knowledge and informed judgment are increasingly required of testing personnel. Further, to meet robust security demands, systems need to be tested not only for what they will do but also for what they will not do.
Security testing has not been properly addressed. Last year, for example, while compliance with all other PCI Data Security Standard requirements had increased, the compliance rate for security testing actually declined - to only 33% of surveyed companies [5]. And these requirements really represent only a lower boundary of what testing can and should be done.
Tester qualifications are built up by means of individual education and experience. These qualifications may then be measured against professional community consensus standards expressed in a body of knowledge. The certification examination should ideally consist of questions that address the full range of expertise from identification and application all the way to analysis and synthesis.
The International Software Testing Qualifications Board (ISTQB) recently approved a new certification for security testers [6]. It would be most helpful for those testers already working to address security issues or individuals trying to develop specialized expertise in security testing.
What are some of the typical business objectives that a certified security tester would be expected to accomplish?
- Plan, perform, and evaluate security tests
- Align security test activities with project lifecycle activities.
- Effectively use risk assessment techniques to identify security threats and their severity.
- Evaluate effectiveness of established security policies, procedures, and mechanisms.
- Help the organization build information security awareness.
- Analyze and select candidate security test tools.
- Select and apply appropriate security testing standards and guidelines.
Certified Security Testers should be able to demonstrate their skills in performing tasks such as:
- Evaluate an existing security test suite and identify any additional security tests needed.
- Identify security test objectives based on functionality, technology attributes, and known vulnerabilities.
- Analyze a given situation and determine which security testing approaches are most likely to succeed in that situation.
- Demonstrate the attacker mentality by discovering key information about a target, performing actions on a test application in a protected environment that a malicious person would perform, and understand how evidence of the attack could be deleted.
- Analyze and document security test needs to be addressed by one or more tools.
The wide range of insight and involvement required of a security tester is reflected in the content of the certification syllabus [7].
- The Basis of Security Testing addresses risks, policies and procedures, and the role of auditing in testing.
- Defining objectives, evaluating different test approaches, and identifying stakeholders are some of the concerns under Security Test Purposes, Goals and Strategies.
- Test planning, design, execution, and maintenance are detailed as Security Testing Processes.
- It is clear that security must be "built in" during system development and not "tacked on" at the end, so there are many specifics of Security Testing Throughout the Application Lifecycle.
- Testing Security Mechanisms assesses the appropriateness and strength of defensive measures such as system hardening, encryption, malware scanning, and intrusion detection.
- Defenders needs to know what they are defending against, so Human Factors in Security Testing includes material on threat analysis and social engineering.
- The importance of Security Test Evaluation and Reporting are documents, as is the proper selection and use of Security Testing Tools.
- Given the constantly evolving threats and expectations one needs to remain conversant with Standards and Industry Trends on an ongoing basis.
Investment in security testing is a proven means of reducing the likelihood and severity of security failures. The greatest return on that investment comes when the testing is done with maximum efficiency … and that, in turn, depends on testers who are skilled and knowledgeable in the most up-to-date threats and countermeasures.
Individuals pursuing ISTQB certification as a security tester are enhancing their own professionalism and value. A company employing certified security testers is positioning itself to better weather the storms that are only going to strengthen in the future.
- The Security Tester certification is positioned as a "specialist" certificate at the Advanced Level, meaning a candidate must first submit proof of Foundation certification (CTFL) and a resume and/or employer verification of 3 years experience.
- The exam for Advanced Level "Security Tester" has 45 multiple-choice questions to be completed in two hours. Value of the questions is weighted on the basis of their difficulty as measured by knowledge level (corresponding to Bloom's taxonomy of the cognitive domain).
- Further information is available at https://www.astqb.org/advanced-tester/ and exam registration may be done at https://www.astqb.org/get-certified/istqb-software-tester-certification-exam-registration/
[1] www.ponemon.org/local/upload/file/Consumer Study on Aftermath of a Breach FINAL 2.pdf
[2] "The Need for Greater Focus on the Cybersecurity Challenges Facing Small and Midsize Businesses" at www.sec.gov/news/statement/cybersecurity-challenges-for-small-midsize-businesses.html
[3] National Small Business Association, 2014 Year-End Economic Report, 16 (2015), available at http://www.nsba.biz/wp-content/uploads/2015/02/Year-End-Economic-Report-2014.pdf
[4] National Cyber Security Alliance, America's Small Businesses Must Take Online Security More Seriously (Oct. 2012), available at www.staysafeonline.org/stay-safe-online/resources/small-business-online-security-infographic
[5] http://www.csoonline.com/article/2895772/data-protection/verizon-report-security-testing-compliance-down-from-last-year.html
[6] http://www.istqb.org/certification-path-root/advanced-security-tester/advanced-security-tester-contents.html
[7] https://www.astqb.org/documents/Advanced-Security-Tester-Syllabus-GA-2016.pdf
|


